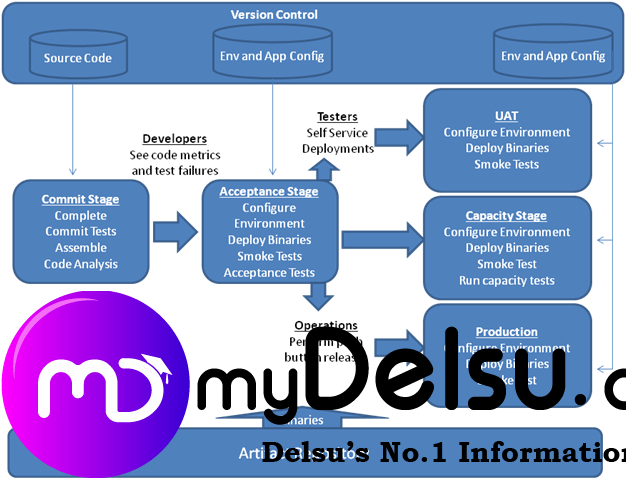
When it comes to understanding the state of deployment, many factors come into play. From analyzing the efficiency of project management to gauging the availability of resources, the journey of deployment is influenced by a multitude of variables. In this article, we will explore the intricate process behind determining the state of deployment and uncover the key elements that contribute to its success. Whether you’re a seasoned professional or new to the field, join us as we unravel the mysteries of deployment and discover how organizations assess its state.

This image is property of www.worldofagile.com.
1. Defining Deployment
1.1 The concept of deployment
Deployment refers to the process of putting a system or solution into operational use. It involves the implementation of the necessary resources, technologies, and strategies to ensure the successful execution of a project or initiative. Deployment encompasses various activities, such as setting up infrastructure, integrating software and hardware components, and training end-users.
1.2 Importance of deployment in various fields
Deployment plays a crucial role in various fields, including technology, healthcare, manufacturing, and more. In the technology sector, deployment is essential for rolling out software applications, hardware systems, and network infrastructure. In healthcare, deployment enables the implementation of electronic medical records systems, medical devices, and telemedicine solutions. Similarly, the manufacturing industry relies on deployment to introduce automation systems, production equipment, and quality control processes.
1.3 Key objectives of deployment
The primary objectives of deployment are to ensure a smooth transition from development to production, optimize the performance and reliability of the deployed system, and achieve user satisfaction. Additionally, deployment aims to minimize disruption to ongoing operations, mitigate risks and challenges, and maximize the return on investment. It involves careful planning, coordination, and execution to achieve these goals effectively.
2. Factors Affecting Deployment Decisions
2.1 Organizational considerations
Organizational considerations heavily influence deployment decisions. These include factors such as company culture, organizational structure, and strategic priorities. It is important to align the deployment strategy with the overall objectives and values of the organization. The decision-makers need to assess the readiness of the organization for change and ensure that there is sufficient support from leadership and key stakeholders.
2.2 Resource availability
The availability of resources, including financial, personnel, and technological, significantly impacts the deployment process. Adequate funding must be allocated for infrastructure setup, software and hardware procurement, and training programs. Sufficient skilled personnel should be allocated to manage the deployment activities effectively. Furthermore, the availability and compatibility of the required technological resources must be evaluated to ensure a seamless deployment.
2.3 Technological requirements
The technological requirements of the deployment must be thoroughly evaluated. This includes assessing the compatibility of the solution with existing systems and infrastructure, as well as the scalability and performance capabilities of the technology. It is important to consider factors such as hardware and software specifications, data storage and processing requirements, network connectivity, and integration capabilities. Failure to address these technological considerations can result in deployment issues and suboptimal performance.
2.4 Stakeholder expectations
Stakeholder expectations are critical in determining the deployment strategy. Identifying key stakeholders and understanding their needs, concerns, and desired outcomes is essential. This includes end-users, management, IT personnel, and regulators, among others. By considering stakeholder expectations, the deployment can be tailored to meet specific requirements and address potential challenges. Effective communication and collaboration with stakeholders throughout the deployment process are crucial for project success.
2.5 Cost-benefit analysis
Conducting a cost-benefit analysis is vital to evaluate the financial feasibility of the deployment. This analysis involves comparing the anticipated costs, including upfront expenses and ongoing maintenance costs, with the expected benefits and return on investment. It helps in determining the financial viability of the project and making informed decisions regarding resource allocation, budgeting, and procurement. Consideration should also be given to potential cost optimization strategies to minimize expenses without compromising the quality and effectiveness of the deployment.
3. Evaluating Readiness for Deployment
3.1 Assessing infrastructure
Before deployment, the infrastructure readiness needs to be assessed. This includes evaluating the availability and suitability of the physical space, power supply, and network infrastructure required for the system to operate effectively. It also involves assessing any necessary upgrades or modifications to the existing infrastructure. By ensuring that the infrastructure is adequately prepared, potential issues and disruptions during deployment can be minimized.
3.2 Testing and quality assurance
Thorough testing and quality assurance are essential to determine readiness for deployment. Rigorous testing should be conducted to identify any defects, bugs, or performance issues in the system. This includes functional testing, performance testing, security testing, and user acceptance testing. The quality assurance process ensures that the system meets the specified requirements, performs reliably, and is ready for production use. Any identified issues should be resolved before proceeding with deployment.
3.3 Training and skill development
End-user training and skill development are critical aspects of deployment readiness. Users need to be adequately trained on the functionalities and usage of the deployed system. This includes providing training materials, conducting training sessions, and offering support for any questions or issues that may arise. By ensuring that the users are proficient in utilizing the system, the effectiveness and adoption of the deployment can be enhanced.
3.4 Change management planning
Change management planning is crucial to ensure a smooth transition to the deployed system. It involves developing a comprehensive plan to address the impact of the deployment on the organization, employees, and processes. This includes identifying potential resistance to change, communicating the benefits of the deployed system, and implementing strategies to alleviate concerns. Effective change management planning helps in minimizing disruption, maximizing user acceptance, and facilitating a successful deployment.
3.5 Risk assessment and mitigation
Risk assessment and mitigation activities are essential in evaluating the readiness for deployment. Potential risks and challenges should be identified and evaluated, considering factors such as technical feasibility, security vulnerabilities, and regulatory compliance. Strategies should be developed to mitigate these risks and address any potential issues that may arise during deployment. Regular risk assessments should be conducted throughout the deployment process to ensure that mitigation plans are effective and up-to-date.
4. Determining Suitable Deployment Strategies
4.1 Agile deployment approach
The agile deployment approach emphasizes iterative and incremental delivery of the solution. It involves breaking down the deployment process into smaller, manageable phases. This allows for regular feedback and adaptation to changing requirements. The agile deployment approach is particularly suitable for projects that require flexibility, quick response to market changes, and continuous improvement. It offers greater adaptability and collaboration between development teams and stakeholders.
4.1.1 Continuous deployment
Continuous deployment is a subset of the agile approach that focuses on the frequent and automated release of new features and updates. It involves integrating development and deployment processes to enable rapid delivery and feedback loops. Continuous deployment is well-suited for software applications and services that require regular updates and enhancements based on user feedback and market demands. It enables organizations to respond quickly to emerging needs and stay ahead of the competition.
4.1.2 Incremental deployment
Incremental deployment involves deploying the solution in small increments, gradually adding features and functionality over time. This approach allows for early user feedback, helps manage risks, and allows for incremental improvements based on user needs. It is particularly useful when a complete solution cannot be deployed at once or when there is uncertainty about specific requirements. Incremental deployment enables organizations to quickly deliver value to users and continuously refine the system.
4.1.3 Kanban deployment
Kanban deployment is a visual approach to deployment management. It involves creating a Kanban board to track the progress of deployment tasks, identify bottlenecks, and improve overall efficiency. Kanban deployment provides a clear and transparent view of the deployment process, ensuring that tasks are completed in a timely manner. It allows teams to prioritize and manage work effectively, enhancing collaboration and facilitating continuous improvement.
4.2 Waterfall deployment approach
The waterfall deployment approach follows a sequential and linear process, with distinct phases such as requirements gathering, design, development, testing, and deployment. Each phase must be completed before proceeding to the next, and changes are difficult to incorporate once a phase is completed. This approach is suitable for projects with well-defined requirements and where changes are unlikely. It provides a structured and disciplined approach to deployment.
4.2.1 Big bang deployment
Big bang deployment involves deploying the entire solution at once, without any phased approach. This approach requires significant planning and coordination to ensure a seamless transition. It is best suited for projects where the entire solution can be implemented simultaneously, and the impact on existing processes and systems is minimal. Big bang deployment offers the advantage of a quick and comprehensive deployment but can also carry higher risks due to the lack of a gradual rollout.
4.2.2 Phased deployment
Phased deployment involves dividing the deployment process into distinct phases or stages, with each phase building upon the previous one. This approach allows for incremental deployment of functionalities and facilitates better risk management. It enables organizations to prioritize critical components, test and refine the system in stages, and address any issues before proceeding to the next phase. Phased deployment provides more control and allows for gradual adoption of the system.
4.3 Hybrid deployment approach
The hybrid deployment approach combines elements of both agile and waterfall approaches. It involves tailoring the deployment strategy based on the nature of the project and the specific requirements. This approach allows organizations to leverage the benefits of each approach and adapt to the unique circumstances of the project. Hybrid deployment provides flexibility, enabling organizations to respond to changing needs while maintaining structure and control.
4.3.1 Combining agile and waterfall approaches
Combining agile and waterfall approaches involves using agile principles for certain aspects of the deployment, such as requirements gathering, development, and testing, while adopting a more sequential approach for other phases, such as infrastructure setup and training. This hybrid approach allows for quicker iteration and responsiveness in areas that benefit from agility while maintaining a structured and controlled process in other areas. It offers a balance between adaptability and discipline.

This image is property of codefresh.io.
5. Impact of Technology and Infrastructure
5.1 Assessing technology readiness
Assessing technology readiness is crucial to ensure that the deployed system can effectively operate within the existing technology landscape. It involves evaluating the compatibility of the solution with the organization’s infrastructure, software, and hardware. This assessment helps identify any potential integration challenges or limitations that may impact the deployment. By addressing technology readiness, organizations can avoid compatibility issues and ensure a seamless deployment process.
5.2 Matching infrastructure capabilities
Matching infrastructure capabilities with the requirements of the deployed system is essential for its successful operation. This involves evaluating factors such as computing power, storage capacity, network bandwidth, and scalability. The infrastructure must be able to handle the expected workload and provide the necessary resources for optimal performance. By matching infrastructure capabilities with system requirements, organizations can avoid performance bottlenecks and ensure a reliable and efficient deployment.
5.3 Scalability considerations
Scalability considerations are crucial in determining the long-term viability of the deployment. Organizations need to evaluate the scalability of the deployed system to accommodate future growth and changing demands. This includes assessing the system’s ability to handle increased data volumes, user traffic, and processing requirements. Scalability ensures that the system can grow and adapt without significant disruptions or the need for a complete overhaul. It allows organizations to future-proof their deployments and avoid potential limitations.
5.4 Compatibility and integration challenges
Compatibility and integration challenges can arise during deployment due to the need to integrate the deployed system with existing systems and processes. The compatibility of the deployed solution with other technology platforms, databases, and software applications must be carefully evaluated. Integration challenges can include data mapping, format conversions, API integrations, and synchronization. Addressing compatibility and integration challenges is crucial to ensure smooth data flow, interoperability, and seamless operation.
5.5 Security and data privacy concerns
Security and data privacy concerns must be taken into account during deployment. The deployed system should meet appropriate security standards and comply with relevant privacy regulations. This includes implementing authentication mechanisms, encryption protocols, access controls, and data protection measures. Addressing security and privacy concerns mitigates the risk of data breaches, unauthorized access, and privacy violations. Organizations must prioritize the protection of sensitive information and ensure the trust and confidence of users.
6. Managing Stakeholder Expectations
6.1 Identifying key stakeholders
Identifying key stakeholders is critical in managing their expectations effectively. Stakeholders can include end-users, management, IT personnel, customers, vendors, and regulatory bodies. Each stakeholder group may have different needs, concerns, and priorities. By identifying key stakeholders, their roles and responsibilities can be clearly defined, ensuring effective communication and engagement throughout the deployment process.
6.2 Defining their expectations
Once key stakeholders are identified, their expectations must be clearly defined. This involves understanding their desired outcomes, concerns, and requirements from the deployment. For example, end-users may expect improved productivity and user experience, while management may focus on cost savings and competitive advantage. By defining stakeholder expectations, organizations can tailor the deployment strategy to meet specific needs and ensure stakeholder satisfaction.
6.3 Communicating deployment plans
Transparent and timely communication of deployment plans is crucial for effective stakeholder management. This involves sharing clear and concise information about the deployment timeline, objectives, and impact on stakeholders. Communication channels can include meetings, presentations, emails, newsletters, and project management tools. By keeping stakeholders informed, organizations can address any potential misconceptions or resistance, build trust, and ensure stakeholder buy-in.
6.4 Addressing concerns and feedback
Addressing stakeholder concerns and feedback is essential for successful deployment. Active listening and open communication channels should be established to encourage stakeholders to voice their concerns and provide feedback. By addressing these concerns promptly and effectively, organizations can mitigate resistance to change, gain valuable insights, and make necessary adjustments to the deployment plan. Stakeholder concerns should be acknowledged and dealt with in a transparent and empathetic manner.
6.5 Ensuring stakeholder engagement
Ensuring stakeholder engagement throughout the deployment process is crucial for user adoption and project success. Stakeholders should be involved in decision-making, testing, and training activities. Their input and feedback should be actively sought and considered. By involving stakeholders in the deployment process, organizations can enhance user acceptance, gather valuable insights, and foster a sense of ownership and commitment to the deployed system.

This image is property of images05.military.com.
7. Financial Considerations
7.1 Budget allocation for deployment
Budget allocation for deployment is a critical aspect of financial planning. Adequate funding must be allocated for various aspects of the deployment, including infrastructure setup, resource acquisition, training programs, quality assurance activities, and ongoing maintenance. It is important to conduct a thorough cost estimation and consider any potential unexpected expenses. A well-defined budget ensures that the necessary resources are available and helps in avoiding financial constraints during the deployment process.
7.2 ROI analysis
Conducting a return on investment (ROI) analysis is vital to assess the financial viability of the deployment. This analysis involves comparing the anticipated benefits and expected returns with the projected costs. Quantifiable benefits, such as cost savings, increased productivity, and revenue generation, should be evaluated. By assessing the ROI, organizations can make informed decisions regarding resource allocation, prioritize deployment initiatives, and justify the investment to stakeholders.
7.3 Cost optimization strategies
Implementing cost optimization strategies can help organizations reduce unnecessary expenses during deployment. This includes evaluating alternative solutions or vendors, negotiating favorable contracts, adopting open-source software, and optimizing resource utilization. Cost optimization should be balanced with quality and effectiveness to ensure a successful deployment. By identifying opportunities for cost optimization, organizations can maximize the value of their investment and minimize financial risks.
7.4 Long-term maintenance and support costs
Long-term maintenance and support costs must be considered during the deployment planning phase. This includes ongoing software updates, hardware maintenance, user support, and system monitoring. Organizations should estimate these costs and factor them into the budget and financial projections. By planning for long-term maintenance and support, organizations can ensure the continued operation and performance of the deployed system, mitigate potential disruptions, and minimize the total cost of ownership.
7.5 Procurement and vendor management
Procurement and vendor management play a crucial role in the financial considerations of deployment. Organizations need to evaluate potential vendors, negotiate contracts, and ensure transparency and accountability in vendor relationships. This includes assessing vendor capabilities, evaluating pricing models, and establishing service level agreements. Efficient procurement and vendor management practices help organizations optimize costs, manage risks, and ensure the quality and reliability of the deployed system.
8. Addressing Risks and Challenges
8.1 Identifying potential risks
Identifying potential risks is a critical step in effective risk management during deployment. Risks can include technical issues, resource constraints, schedule delays, stakeholder resistance, security vulnerabilities, and regulatory compliance challenges. A thorough risk assessment should be conducted to identify and evaluate these risks in terms of their likelihood of occurrence and potential impact. By proactively identifying risks, organizations can develop mitigation plans and contingency strategies.
8.2 Creating risk mitigation plans
Creating risk mitigation plans involves developing strategies to minimize the likelihood and impact of identified risks. This includes implementing preventive measures, such as conducting thorough testing, implementing security controls, and providing user training. Additionally, organizations should develop contingency plans to address unforeseen risks and disruptions. Risk mitigation plans should be documented, communicated to stakeholders, and regularly reviewed and updated throughout the deployment process.
8.3 Contingency planning
Contingency planning is crucial to ensure preparedness for unforeseen events and mitigate potential disruptions during deployment. This involves developing alternative strategies and backup plans to address potential risks and challenges. Contingency plans can include backup systems, redundant infrastructure, alternative resource allocation, and communication protocols. By having contingency plans in place, organizations can respond effectively to unexpected situations and ensure the continuity of operations.
8.4 Monitoring and addressing challenges
Continuous monitoring of the deployment process is essential to identify and address emerging challenges promptly. This includes tracking key performance indicators, conducting regular progress reviews, and soliciting feedback from stakeholders. By proactively monitoring the deployment, organizations can identify any deviations from the planned schedule, performance issues, or user dissatisfaction. Prompt action can be taken to address these challenges and ensure a successful deployment.
8.5 Post-deployment evaluation
Post-deployment evaluation is crucial to assess the effectiveness of the deployment and identify opportunities for improvement. This involves conducting a thorough review of the deployed system’s performance, user satisfaction, and achievement of objectives. Feedback from end-users, stakeholders, and the deployment team should be gathered to identify any areas of concern or potential enhancements. The insights gained from the post-deployment evaluation can inform future deployments and continuous improvement initiatives.

This image is property of codefresh.io.
9. Ensuring User Adoption and Satisfaction
9.1 User training and onboarding
Ensuring user training and onboarding is essential to promote user adoption and satisfaction. Comprehensive training programs should be developed to educate users on the functionalities, features, and best practices of the deployed system. Training should be tailored to different user groups and their specific needs. Onboarding activities, such as user orientation sessions and providing user guides or tutorials, can also facilitate a smooth transition to the new system. By investing in user training and onboarding, organizations can enhance user acceptance and minimize resistance to change.
9.2 User feedback and support
Continuously soliciting user feedback and providing ongoing support are critical for user satisfaction. Organizations should establish channels for users to provide feedback, such as help desks, support tickets, or user forums. User concerns, questions, and issues should be promptly addressed to minimize frustration and maximize productivity. By actively engaging with users and addressing their needs, organizations can improve the user experience, identify opportunities for system enhancements, and foster a positive user perception of the deployed system.
9.3 Continuous improvement initiatives
Continuous improvement initiatives are vital to ensure the relevance and effectiveness of the deployed system over time. Organizations should establish processes to collect user feedback, analyze system performance, and identify areas for improvement. This can involve conducting regular system audits, prioritizing enhancement requests, and deploying iterative updates. By continuously iterating and refining the deployed system, organizations can align it with evolving user needs, stay competitive, and maximize user satisfaction.
9.4 User satisfaction surveys
Conducting user satisfaction surveys is an effective way to gauge user perception and identify areas for improvement. Surveys should be designed to capture feedback on various aspects of the deployed system, including usability, performance, and functionality. The insights gained from user satisfaction surveys can help organizations identify strengths and weaknesses, validate deployment objectives, and prioritize improvement initiatives. By prioritizing user satisfaction, organizations can enhance user adoption, productivity, and overall success of the deployment.
9.5 Iterative updates and enhancements
Iterative updates and enhancements are important for keeping the deployed system aligned with changing user needs and technological advancements. Organizations should establish processes to collect user feedback, monitor industry trends, and prioritize system improvements. Regular updates, based on user feedback and market demands, ensure the ongoing relevance, performance, and security of the deployed system. By regularly enhancing the system, organizations can maintain user engagement, optimize system capabilities, and future-proof the deployment.
10. Future-proofing the Deployment
10.1 Scalability and flexibility considerations
Scalability and flexibility considerations are crucial for future-proofing the deployment. Organizations should evaluate the system’s scalability to accommodate future growth and changing demands. This includes assessing factors such as data volume, user traffic, and integration capabilities. Flexibility should also be prioritized, allowing for seamless integration with emerging technologies and evolving business processes. By considering scalability and flexibility, organizations can ensure that the deployment can adapt to future needs and technological advancements.
10.2 Technology roadmap planning
Developing a technology roadmap is essential to guide future deployment initiatives. The roadmap should outline the organization’s strategic vision, technology direction, and key milestones. It should consider emerging technologies and industry trends, aligning them with the organization’s objectives and capabilities. Technology roadmap planning enables organizations to prioritize future deployments, ensure compatibility with existing systems, and optimize resource allocation. It provides a roadmap for future-proofing the deployment and staying ahead of technological advancements.
10.3 Upgrading and modernization strategies
Upgrading and modernization strategies are crucial for maintaining the effectiveness and relevance of the deployed system over time. Organizations should establish processes for regular system audits and evaluate the need for upgrades or modernization periodically. This includes assessing the compatibility of the deployment with the latest software versions, hardware advancements, and industry standards. Upgrading and modernizing the system as necessary helps organizations leverage new technologies, enhance security, and improve system performance.
10.4 Adaptation to evolving needs
The ability to adapt to evolving needs is essential for future-proofing the deployment. Organizations should anticipate changes in user requirements, market dynamics, and regulatory environments. This involves monitoring industry trends, engaging with stakeholders, and staying informed about emerging technology and business trends. By being proactive in adapting to evolving needs, organizations can align the deployment with changing requirements, achieve a competitive edge, and meet user expectations over the long term.
10.5 Embracing emerging technologies
Embracing emerging technologies is critical for future-proofing the deployment. Organizations should regularly evaluate new technologies and assess their potential impact on the deployed system. This includes exploring technologies such as artificial intelligence, machine learning, Internet of Things, and cloud computing. By embracing emerging technologies, organizations can enhance the capabilities and functionalities of the deployed system, drive innovation, and gain a competitive advantage. It allows organizations to stay at the forefront of technological advancements and ensure the longevity of the deployment.
In conclusion, deployment is a complex and multifaceted process that requires careful planning, evaluation, and execution. By considering the factors influencing deployment decisions, evaluating readiness, determining suitable deployment strategies, addressing technological and infrastructure requirements, managing stakeholder expectations, considering financial implications, addressing risks and challenges, ensuring user adoption and satisfaction, and future-proofing the deployment, organizations can increase the likelihood of a successful deployment and derive maximum value from their investment. Collaboration and effective communication among all stakeholders throughout the deployment process are critical for achieving deployment objectives and driving continuous improvement.

This image is property of ops.fhwa.dot.gov.
Didn't find what you were looking for? Search here